Machine learning unlocks a universe of new possibilities – in medical research, for example, or in financial fraud protection. But training machine learning models requires vast pools of real-world data. In both cases used as examples here, the data is highly sensitive, and there are regulations in place to keep it private and secure.
The concept of “confidential computing” was devised to get around this issue. It uses hardware-level memory protection to work with encrypted data without exposing it to the rest of the system. In November, Microsoft announced it was bringing confidential computing built into Azure infrastructure to Kubernetes clusters.
Its open-source Open Enclave SDK lets you create trusted execution environments (TEEs) on IoT devices and, with the Open Enclave SDK Plugin, in Kubernetes-managed containers, using secure hardware, such as Arm TrustZone or Intel SGX (Software Guard Extensions), to isolate workloads that process sensitive data.
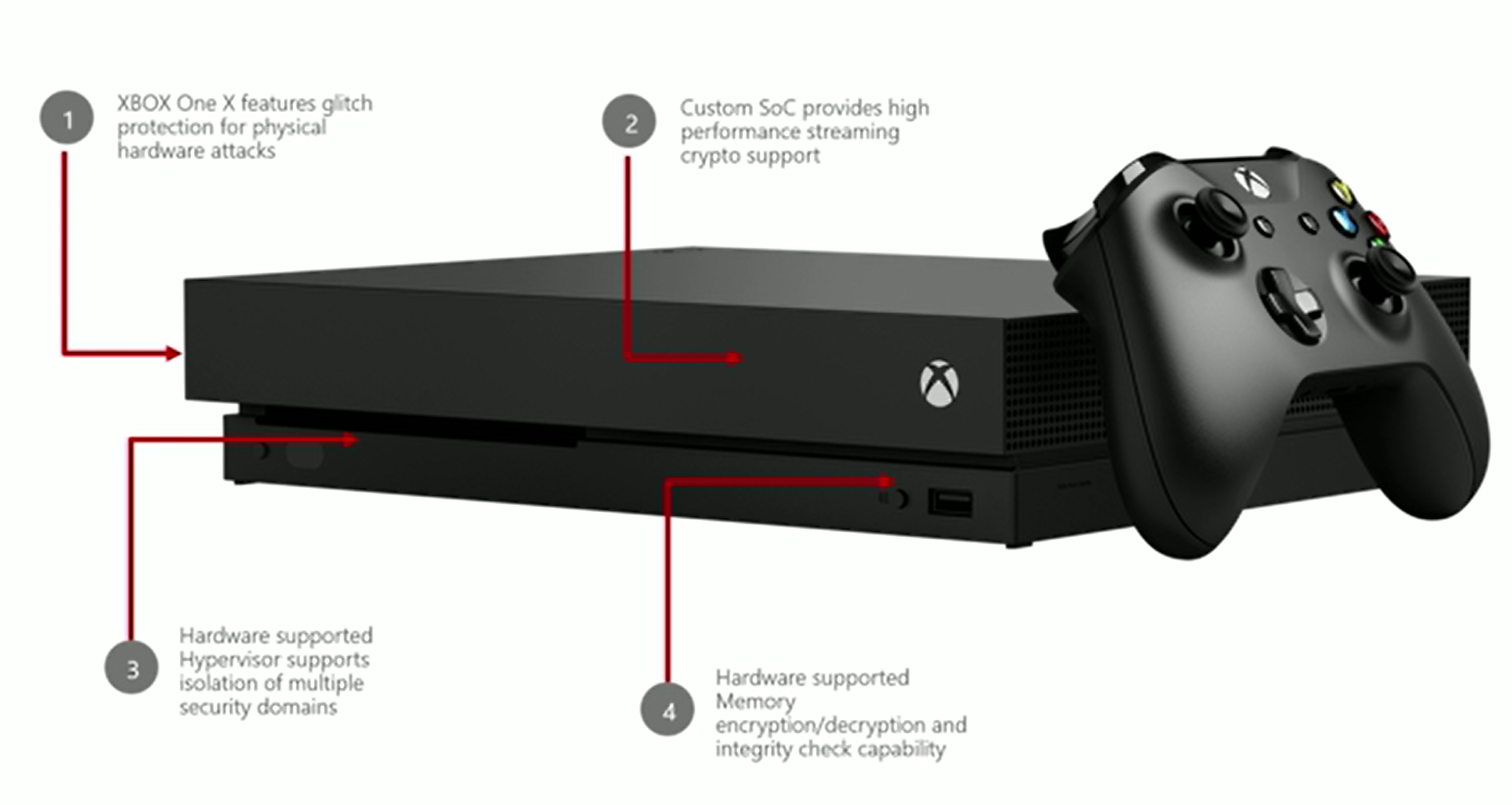
A lot of the engineering work that went into the solution was done for what Dave Weston, director of OS security at Microsoft, called “the most secure product Microsoft has ever produced and maybe the most secure [device] out there:” the Xbox One.
The gaming console has a custom SOC with hardware keys fused into it at the factory (so they can’t be extracted), a high-performance streaming cryptography processor, and hardware hypervisor support. It runs every game in a separate security domain, with the host OS in another, using a tiny version of Hyper-V, isolating credentials and encryption keys in the same way Azure does, so even the machine admin can’t get at them. It also uses hardware-supported memory encryption throughout the platform, which Weston described as “very similar to Azure Confidential Computing.”
If the Xbox isn’t secure, “no-one is going to pay for video games,” he said. But the same concepts of secure enclaves and hardware-protected memory can protect financial, medical, and industrial computing.
Protected Data May Hold Big Insights
Medical datasets are extremely privacy-sensitive, “and yet inside those datasets lie insights that we can unlock that can be used to help advance medical care for everyone,” Gabe Monroy, director of Azure Compute at Microsoft, told Data Center Knowledge. “With this technology, we're now making it possible to run a model and do analysis on these datasets in a way where people can share the data but also get the assurance that you're not violating these privacy concerns.”
Similarly, financial services firms can pool data to train fraud-detection models across a myriad of payment datasets while staying within the privacy compliance guardrails. “There's just a whole host of workloads” that could use the technology, Monroy said.
“Through this device-driver plugin (the Open Enclave SDK Plugin) we’re bringing a level of security assurance down to the metal, down to the chip,” he said. “What is happening at the chipset level has the opportunity to provide a level of assurance that you just can't get with a software-based solution.”
How Trustworthy are Trusted Enclaves?
As software security improves, attackers are focusing their attention on hardware, including security hardware. Researchers have found vulnerabilities in Arm’s TrustZone and Intel SGX, but there are also some built-in protections.
The most recent SGX vulnerability has the catchy but misleading name of Plundervolt. The contents of the enclave aren’t exposed as they could be with the Specter and Foreshadow speculative execution flaws. Instead, they are corrupted by reducing the voltage sent to the CPU while it’s executing enclave computations. Those voltage tweaks require root access on the server and are disabled by the microcode and BIOS updates Intel released as a fix.
Corrupting data would certainly be an issue for a secure workload like confidential computing, but mainly as a denial of service. SGX includes an attestation infrastructure, so workloads can verify the security state on an enclave and enforce policy on whether to trust it or not.
The Xbox One system has built-in protection for voltage manipulation, in case gamers use mod chips to load code that bypasses the game security. But this protection is rather final: it blows fuses and makes the device unusable.
Enclaves are designed to let you work with data in memory without having to worry about that memory being exposed to an attack. SGX uses both CPU instructions and a hardware Memory Encryption Engine to protect data as it leaves the CPU.
“Its role is to help protect the confidentiality, integrity, and freshness of the CPU-DRAM traffic over a configurated memory range,” Anil Rao, Intel VP for Data Center Security and Systems Architecture, explained to Data Center Knowledge.
Enclaves aren’t designed to protect against side-channel attacks on the cache line; it’s about being able to rely on encryption keys derived from hardware keys to protect information and communicate securely between enclaves, he added. Trusted Execution Environments “provide a form of isolation for code and data in such a way that the code and data are cryptographically isolated from other code or operators.”
“A TEE cannot protect you against all forms of attack, but combined with other common security best practices, it adds a powerful additional layer of data protection,” Rao suggested. You probably don’t want to blow the fuses in your Kubernetes cluster if you find signs of tampering the way an Xbox One does, but the attestation should mean you’ll know it’s no longer a trusted environment.





