History will show that Microsoft’s biggest marketing push in the decade of the 2010s — unless the company comes up with a huge surprise right at the buzzer — will have been a design motif. At one point called “Metro,” until a lawsuit forced the company to stop using that word, it’s the idea that people accept information better when it’s summarized and partitioned in rows or columns of scrollable rectangles.
When Microsoft sprung its motif onto the public all at once in 2012 with Windows 8, the result was mass confusion, leading to one of consumer technology’s most well-diagnosed failures. But maybe it wasn’t the little rectangles’ fault. The lesson the company appears to have taken from the Windows 8 debacle was that users appreciate change when it comes more gradually.
So as Microsoft moves its data center admins and DevOps customers towards its Operations Management Suite model, first introduced last year, it’s incorporating incremental additions to the new system while simultaneously encouraging continued use of the old one — in this case, System Center.
This week, the company announced the latest of these additions: a security module with links to Azure Security Center. Marketing may not do this new module justice: While OMS Security purports to maintain active, real-time investigation of potential security threats to its customers, its true value to the enterprise may lie much more deeply beneath the little rectangles on the surface.
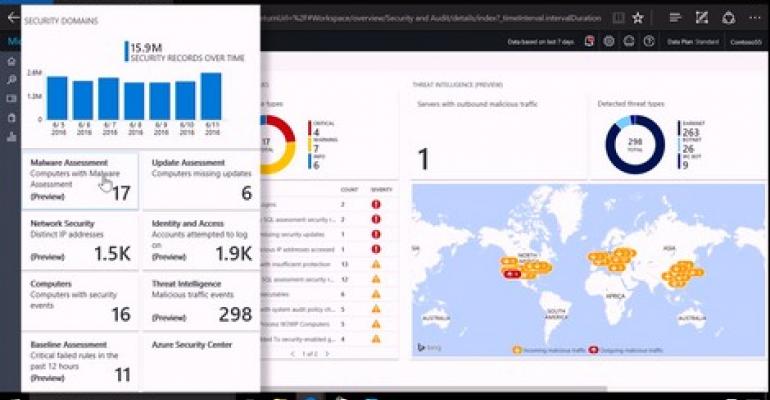
In a company video, Azure Security Principal Program Manager Sarah Fender demonstrated drilling down from the newly amended OMS portal, into a detailed report of the status for particular domains — which in Microsoft’s parlance refers to the general topics to which a business’ security controls may pertain (e.g., units with suspected malware, policy rules that may have failed recently, failed login attempts).
Fender went on to demonstrate a baseline assessment feature, which in an earlier era was not something that a security tool could project in real-time. In the context of OMS, a baseline is a rule that is executed like a policy, and whose result is an event that the console can report.
If you’re a veteran DevOps professional, you’ve already gotten a peek at where we’re going with this: A complex rule execution engine, which includes the generation of custom rules, suggests the presence of a runtime engine that can be extended for something far more applicable than the “user experience:” automation.
Last May, the company began demonstrating the use of PowerShell — the scripting tool that transformed Microsoft’s entire server platform line — in implementing an OMS feature called desired state configuration (DSC). In a similar vein to how Jenkins, the open source CI/CD framework for Linux, utilizes runbooks to automate the delivery of services, Microsoft has been pushing PowerShell over the past few months as a scripting tool for implementing its version of runbooks.
“OMS automation permits me to use PowerShell scripts to automate complex end-to-end processes,” writes certified trainer Ed Wilson (“The Scripting Guy”) in a company blog post last May. “I can do this with runbooks that I can run on demand, run immediately, or that I can schedule to run at a later time. Once I have the PowerShell script in the runbook, I can basically do anything I want to do with that runbook.”
Now, there was an era in Microsoft’s history where the admission that you can do anything you want with Microsoft scripting, would set off red-alert klaxons. But in the spirit in which Wilson meant this in the modern era, he means that PowerShell can implement the goals of DSC because nothing in OMS Automation restricts it from doing so.
It doesn’t take a scripting genius to infer from this that a DevOps or infosec professional could leverage the same system that delivers OMS Automation, to create wide-ranging scripts that assess the security state of domains or data center principals across the globe. Those scripts could, in turn, generate alerts. And while alerts help out the goals of OMS, by way of giving Microsoft something new to animate within the suite’s Web portal, they also give PowerShell runbooks the input they may need to automate security responses in real-time.
While Fender demonstrated the extent to which an operator might see the details of security events in OMS, her demonstration was restricted to what human beings can do in response to those events. The real value of this latest suite addition may yet come from automation that reduces what human beings have to do to respond, to a minimum.