Doug Rollins is a principal SSD systems marketing engineer at Micron Technology, Inc., who holds 13 U.S. patents and is an active member of the Storage Networking Industry Association (SNIA).
Part 1 of this article looked at techniques used to ensure data integrity and optimize performance of enterprise SSDs. This second part takes a look at two additional enterprise-grade SSD features: one is aimed at ensuring data integrity in the event of a sudden power loss; the other helps to increase responsiveness through better background operations management.
Enterprise-class data path protection
Enterprise-class data path protection (eDPP) refers to mechanisms employed inside an enterprise-grade SSD that protect the host data inside the SSD controller. eDPP can be implemented by storing additional information (metadata) along with user data to help ensure that the SSD returns the exact data requested.
Note that data and metadata are very different: data is written and/or read by the host; the logical block address (LBA) for that data (or the location associated with it) is called metadata, which literally means “data about data.” One can think of metadata this way: if the host data was a building, the LBA metadata would be that building’s street address.
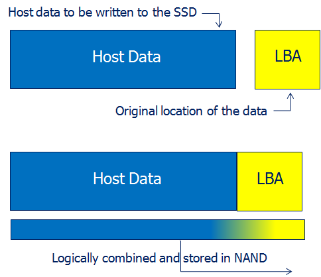
As shown in Figure 3, when the host writes data to the SSD, two key elements combine: the actual data to be written and the LBA from which it came. All data written to the SSD has an LBA associated with it—just like every building has a street address.
By logically combining the host LBA with the associated data before writing the data to the NAND device, the source LBA can be read, checked, and verified when the data is read by the host. This second-level embedding and checking helps guard against data mismatches.
Furthermore, embedding the host LBA as metadata enables more robust power-loss protection. SSDs that use a lookup table to locate data (matching the requested LBA to the NAND page that contains the data) can rebuild that table when power is restored simply by reading the embedded LBA metadata.
In addition to host LBA checking and embedding, eDPP provides other data path protection methods like memory protection ECC (MPECC).
Figure 4 shows how MPECC protects the host data by adding ECC coverage as it enters the DRAM on the SSD. This additional MPECC then follows the host data through the SSD and helps prevent bit fumbling.
Background task management
Background tasks are housekeeping measures performed inside the SSD such as wear management and power loss protection routines. In some SSDs, background tasks can get in the way of servicing host I/O, which can cause unpredictable responses at the application level. However, well-managed background tasks in enterprise-grade SSDs enable faster application response times because they don’t get in the way of processing the intensive host I/O seen in the datacenter. Optimal enterprise-grade SSD design strikes a balance that results in substantially lower maximum WRITE latency at the application level.
An example of two such background tasks are copying any data mapping structures resident in the SSD’s DRAM into the NAND (a process that reduces startup time after a sudden power loss), and wear management.
Enterprise-grade SSDs offer more efficient internal data structures and manage them more granularly— executing background tasks in smaller chunks and ensuring that the operations can be effectively mixed with host I/O processing to optimize both.
Figure 5 shows how wear management can be performed at a very granular level. Managing and moving active data in small chunks facilitates seamless blending with the servicing of host I/O requests. The vertical columns represent NAND blocks and the green dotted area shows the smallest data unit that can be moved to manage wear.
Figure 6 shows an example of a data mapping structure stored in the DRAM of an SSD. In an enterprise SSD, this structure is often logically divided into smaller chunks (8 kilobytes in this example) so that it can be copied to the NAND device more efficiently by interspersing the background operation with host I/O requests. This technique offers better overall performance and superior latency reduction.
Summary
Enterprise-grade SSDs may look similar to client SSDs on the outside, but their internal operations tend to be very different. This two-part article introduced:
- Dynamic read tuning
- NAND die-level redundancy
- Enterprise-grade data path protection
- Optimal background task management
This article also discussed how the key design features of an enterprise-grade SSD can be very specialized. When selecting SSDs for your data center operations, it is imperative that these features and other design elements are well understood by your SSD supplier. Be sure that they can explain how the design works—including each critical element—and how their enterprise-grade design differs from client-grade designs. In short, be a persistent and informed customer before you sign the purchase order.
Industry Perspectives is a content channel at Data Center Knowledge highlighting thought leadership in the data center arena. See our guidelines and submission process for information on participating. View previously published Industry Perspectives in our Knowledge Library.