Cloud computing has given rise to many new types of services for organizations. These include hosting options, data center extensions and even new disaster recovery strategies. With the increase in cloud utilization comes the very real increase in security threats. There’s little doubt that as the size, frequency and complexity of distributed denial of service (DDoS) attacks continue to rise, hosting and cloud service providers must have solutions in place to protect the availability of their infrastructure and services. Now, there are three specific types of attacks which attackers can utilize to bring a system to a halt:
- Volumetric Attacks
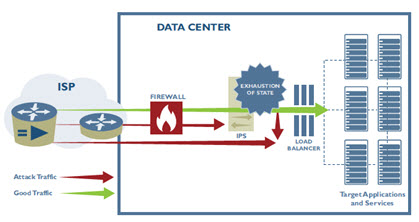
- TCP State-Exhaustion Attacks
- Application-Layer Attacks
In understanding the DDoS attack environment, administrators should know that their current security platform may actually not be designed to protect against DDoS attacks.
As organizations continue to grow their cloud presence, security administrators need to look at other options to help them protect their internal environments as well as their cloud infrastructure. In this white paper from Frost and Sullivan, we learn how Arbor Networks helps an organization create a layered security platform capable of preventing the above three types of DDoS attacks. Specifically, this white paper outlines how an Intelligent DDoS Mitigation Systems (IDMS) can help secure a growing organization. Remember, these solutions were designed from the ground up to detect and stop DDoS attacks. Some of the key characteristics of an IDMS are:
- Support both -inline and, more importantly, out-of-band deployment to avoid being single point of failure on the network.
- True “distributed” DoS (DDoS) attack detection, which requires broad visibility into network (not just from a single network perspective) and the ability to analyze traffic different parts of the network.
- Attack detection using multiple techniques, such as statistical anomaly detection, customizable threshold alerts and fingerprints of known or emerging threats that based on Internet-wide intelligence.
- Mitigation that can easily scale to handle attacks of all sizes, ranging from low-(e.g., 1Gbps) to high end (e.g., 40Gbps).
As data center environments continue to evolve, there will be a greater need for more comprehensive security solutions. Click here to download this white paper to see how Arbor Networks can help remove the threat of botnets, DDoS attaks and create a more robust – and secure – infrastructure.